Yesterday, a researcher disclosed a method of hiding up to three MB of data inside a Twitter image.
In his demonstration, the researcher showed both MP3 audio files and ZIP archives contained within the PNG images hosted on Twitter.
Although the art of hiding non-image data in images (steganography) isn’t novel, the fact that the images can be hosted on a popular website like Twitter and are not sanitized opens up a possibility for their abuse by malicious actors.
An image that sings…
Yesterday, researcher and programmer David Buchanan attached example images to his tweets that had data such as entire ZIP archives and MP3 files hidden within.
Although the attached PNG files hosted on Twitter represent valid images when previewed, merely downloading and changing their file extension was enough to obtain different content from the same file.
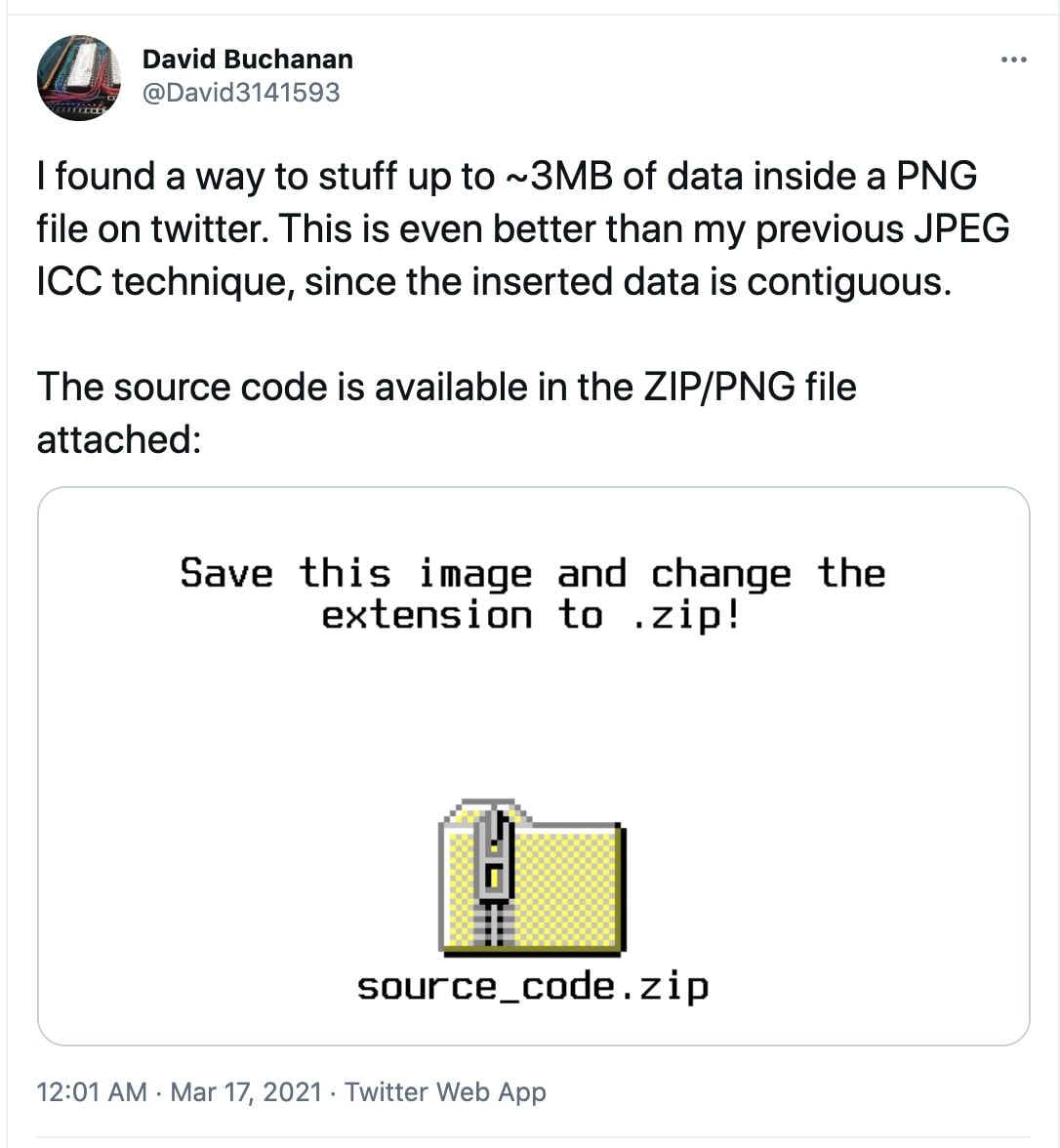
An example image file posted by Buchanan to Twitter contains a ZIP archive within (Source: Twitter)
As you can see the 6 KB image tweeted by the researcher contains an entire ZIP archive.
The ZIP contains Buchanan’s source code that anyone can use to pack miscellaneous contents into a PNG image.

The PNG image tweeted by Buchanan has the structure of a valid ZIP file (Source: BleepingComputer)
For those who prefer the slightly-less hands-on approach, the researcher has also provided source code for generating what he calls https://github.com/DavidBuchanan314/tweetable-polyglot-png">tweetable-polyglot-png files on GitHub.
In another example uploaded to Twitter, Buchanan tweeted an image that could sing.
“Download this one, rename to .mp3, and open in VLC for a surprise. (Note: make sure you download the full resolution version of the file, should be 2048x2048px),” said the researcher.
After testing, the picture located at the Twitter image server below is approximately 2.5 MB in size and can be saved with a “.mp3” extension.
Once opened, the image file, now turned MP3, would start playing the song Never Gonna Give You Up by Rick Astley.
“Twitter does compress images, most of the time, but there are some scenarios where they don’t.”
“Twitter also attempts to strip any non-essential metadata, so any existing ‘polyglot file’ techniques wouldn’t work.”
“The new trick which I discovered, is that you can append data to the end of the ‘DEFLATE‘ stream (the part of the file that stores the compressed pixel data), and Twitter will not strip it,” Buchanan said.
Open to abuse by stealthy threat actors
Steganography techniques are often leveraged by stealthy threat actors as they enable them to hide malicious commands, payload, and other content in ordinary-looking files, such as images.
Just yesterday, BleepingComputer reported on a new exfiltration technique using which cybercriminals were hiding stolen credit card data in JPG images.
The fact that Twitter may not always strip extraneous information from an image, as demonstrated by Buchanan, opens up room for the platform’s abuse by threat actors.
Moreover, what poses an additional challenge is blocking Twitter image traffic may impact legitimate operations.
For example, a network administrator blocking Twitter’s image domain pbs.twimg.com would also cause legitimate images hosted on Twitter to be blocked.
That being said, Buchanan believes his PNG image proof-of-concept technique may not be particularly useful by itself as more steganography methods are viable.
“I don’t think this technique is particularly useful for attackers, because more traditional image steganography techniques are easier to implement (and even more stealthy).”
However, more likely than not, the PNG technique demonstrated by the researcher could be used by malware for facilitating its command-and-control C2 activities.
“But maybe it could be used as part of a C2 system, for distributing malicious files to infected hosts,” Buchanan further said.
Likewise, because Twitter may be considered a safe host by network monitoring systems, malware distribution via Twitter using such image files remains a viable method for bypassing security programs.
When asked if Twitter was aware of this bug, the researcher said:
“I reported my original JPEG-based trick to Twitter’s bug bounty program, but they said it wasn’t a security bug, so I didn’t bother reporting this one to them.”
In his example from 2018, Buchanan had tweeted a tiny JPG thumbnail that contained Project Gutenberg’s huge collection of The Complete Works of William Shakespeare.

The Complete Works of William Shakespeare stored in a tiny JPG file on Twitter (Source: BleepingComputer)
Previously, attackers have misused legitimate services like Imgur to host their images which were later used to calculate malicious Cobalt Strike payload.


