New tools attributed to the Russia-linked Gamaredon hacker group include a module for Microsoft Outlook that creates custom emails with malicious documents and sends them to a victim’s contacts.
The threat actor disables protections for running macro scripts in Outlook and to plant the source file for the spearphishing attacks that spread malware to other victims.
Gamaredon has been in the cyber espionage game since at least 2013, targeting national security institutions in Ukraine for political and military gain. It became more active since December 2019.
Automated spear phishing
A new package used by Gamaredon (Primitive Bear) in recent malicious campaigns contains a Visual Basic for Applications (VBA) project (.OTM file) that targets Microsoft Outlook email client with malicious macro scripts.
Compromising an email account to spread malware to contacts is not a new method but malware analysts at cyber-security company ESET believe that the method used by Gamaredon has not been publicly documented before.
Analyzing the module, the researchers saw that the chain of events starts with a VBScript that terminates the Outlook process.
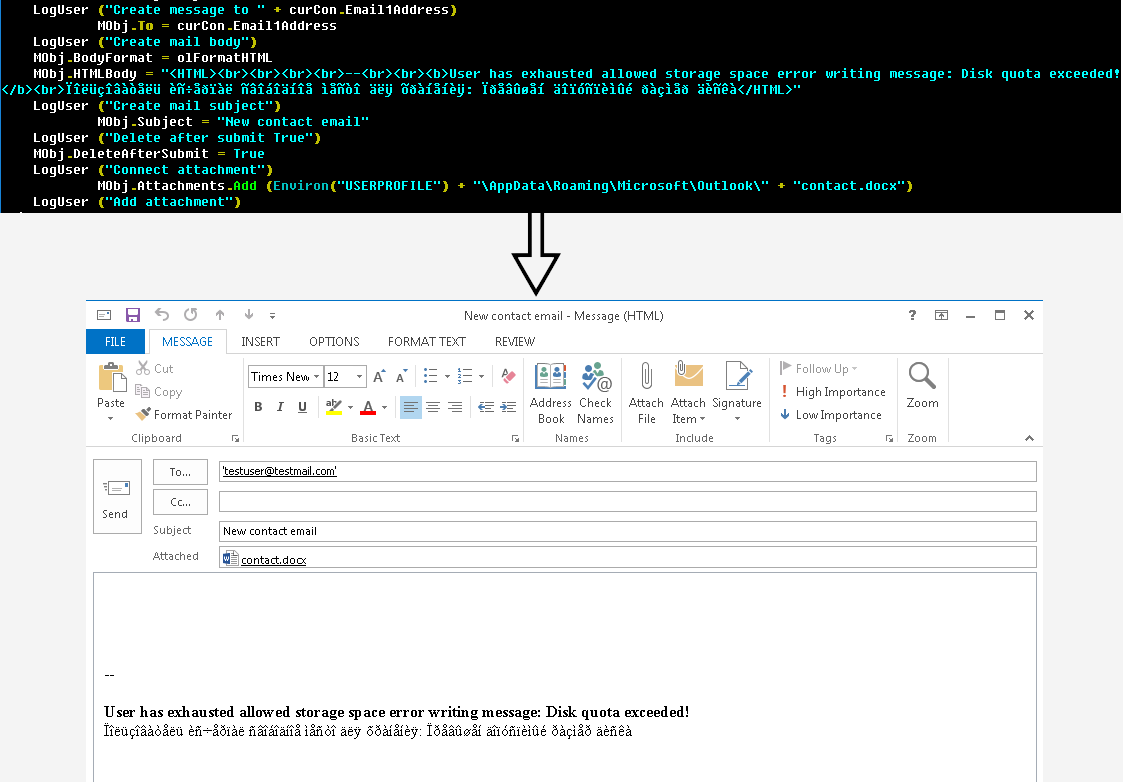
Next, the script modifies registry values to remove security against executing VBA macros in Outlook and stores on the disk a malicious OTM file that helps spread infected documents to email addresses in the contact list.
Outlook supports only one VBA project at a time and the OTM file used in Gamaredon activity contains a VBA script (macro), a malicious email attachment.
Sometimes, it may also include a list of targets that should get the messages. According to ESET, the threat actor may spear phish all contacts in the victim’s address book, everyone in the same organization, or a predefined set of email addresses.
The VBA code is responsible for generating the email complete with body text and malicious files (.DOCX, .LNK).
According to ESET, Gamaredon has multiple variants for CodeBuilder, the module for injecting malicious macros or remote templates in documents available on the infected host.
This method is efficient because documents are often shared within the organization and it also achieves persistence since the files are likely to be opened multiple times.
“These macro injection modules also have the functionality to tamper with the Microsoft Office macro security settings. Thus, affected users have no idea that they are again compromising their workstations whenever they open the documents. We have seen this module implemented in two different languages: C# and VBScript” – ESET
As for the malware spread this way, the researchers note that downloaders and backdoors are the most prevalent. Some are updates for variants seen since 2017 while others are rewrites in a different programming language:
- Downloaders – fetch and execute a malware
- Backdoors and file stealers – enumerate documents and upload them to the command and control (C&C) server; can also download and execute other code from the C&C
- Batch file/VBScript – scan system for Word documents and stores their names in a text file
ESET says that Gamaredon’s scripts are not defined by their quality but the rapid development and volume, which explains the multitude of errors and mistakes noticed by the researchers (e.g. comments in the source code, wrong language encoding).
The information contained in this website is for general information purposes only. The information is gathered from Bleeping Computer, while we endeavour to keep the information up to date and correct, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability or availability with respect to the website or the information, products, services, or related graphics contained on the website for any purpose. Any reliance you place on such information is therefore strictly at your own risk. Through this website, you are able to link to other websites which are not under the control of CSIRT-CY. We have no control over the nature, content and availability of those sites. The inclusion of any links does not necessarily imply a recommendation or endorse the views expressed within them. Every effort is made to keep the website up and running smoothly. However, CSIRT-CY takes no responsibility for, and will not be liable for, the website being temporarily unavailable due to technical issues beyond our control.


